Human-AI SOC Platform
Transforming Cybersecurity Operations with Human + AI Collaboration
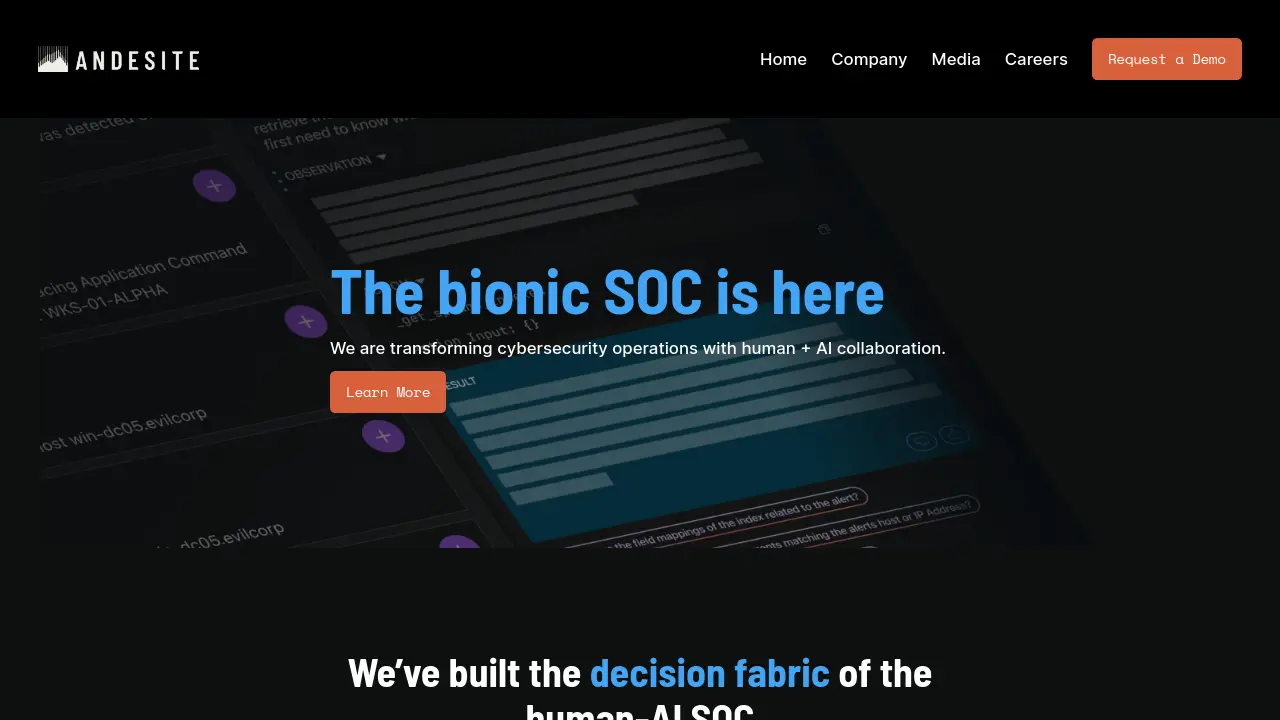
Description
This platform represents a shift towards the 'bionic SOC', integrating artificial intelligence with human expertise to revolutionize cybersecurity operations. It focuses on creating a cohesive decision fabric for SOC teams by leveraging AI to automatically prioritize critical alerts, threat intelligence feeds, and relevant data points. This automation significantly accelerates the investigation and enrichment processes, freeing up human analysts for higher-level tasks.
The core of the platform is an investigation workspace designed for efficiency and collaboration. It allows teams to consolidate data from multiple security tools and sources into a single view without requiring complex ETL processes or data migration. Featuring capabilities like Evidentiary AI™, investigations remain traceable to verified sources, ensuring transparency and facilitating human review. Built with a Safe AI Architecture™ and adhering to numerous security and compliance standards (including FedRAMP High, SOC 2, NIST, ISO, PCI DSS, and HIPAA), it offers both cloud and self-managed on-prem deployment options, ensuring robust data protection and regulatory alignment.
Key Features
- AI-driven Alert Prioritization: Surfaces key alerts, intelligence, and data.
- Automated Investigation & Enrichment: Accelerates and automates investigation workflows.
- Unified Investigation Workspace: Consolidates multiple sources and facilitates collaboration.
- Connected Workstreams & Unified Views: Integrates security platforms and tools without ETL.
- Evidentiary AI™: Ensures AI-driven analysis is traceable and verifiable by humans.
- Safe AI Architecture™: Protects network and data with built-in security guardrails.
- Contextual Awareness: Proactively identifies key indicators and connections within investigations.
- Secure & Compliant Design: Adheres to major security/privacy standards (FedRAMP High, SOC 2, NIST, ISO, etc.).
- Flexible Deployment: Offers both Cloud and self-managed on-prem options.
Use Cases
- Alert Investigation: Access, prioritize, triage, and report on alerts from multiple sources.
- Threat Hunting: Initiate investigations from queries, documents, or URLs to determine threat levels and blast radius.
- Threat Intelligence Operationalization: Investigate intelligence feeds directly, determine relevance, and accelerate detection.
You Might Also Like
Leon
FreeYour open-source personal assistant
StatusSight
FreemiumReal-time outage alerts for the services you rely on
PostCraftAI
Free TrialGrow your audience on LinkedIn using AI
Kubio
FreemiumBuild awesome WordPress sites faster with the help of AI
AI Manager Coach
FreemiumAI-Powered Guidance for First-Time Management Challenges